- Information
- AI Chat
Andrew S. Tanenbaum - Computer Networks-10
Python Programming Lab (SOC-2)
Adithya Institute of Technology
Preview text
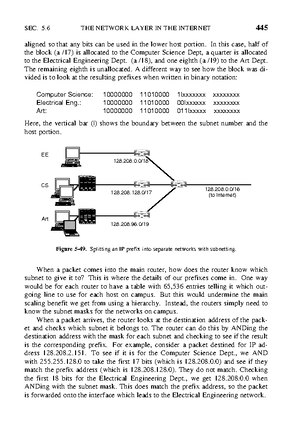
58 INTRODUCTION CHAP. 1
node by a team led by Len Kleinrock (a pioneer of the theory of packet switching) to the SRI node. The network grew quickly as more IMPs were delivered and installed; it soon spanned the United States. Figure 1-27 shows how rapidly the ARPANET grew in the first 3 years.
MIT
UCLA UCLA RAND BBN
SRI UTAH ILLINOIS MIT LINCOLN CASE
CARN
RAND BBN HARVARD BURROUGHS
SDC STAN
UCLA
SRI UTAH
UCSB SDC UCSB
SRI UTAH
UCSB
NCAR GWC LINCOLN CASE
MITRE ETAC RAND TINKER BBN HARVARD NBS
SDC
AMES USC STAN
UCLA
CARN
SRI UTAH
MCCLELLAN
UCSB
ILLINOIS LINC
RADC
MIT
ILLINOIS MIT
LINC
RADC
UTAH
RAND TINKER
SRI LBLMCCLELLAN
AMES TIP X-PARCAMES IMP
FNWC
UCSB UCSD
STANFORD
CCA BBN HARVARD ABERDEEN NBS ETAC ARPA MITRE SAAC BELVOIR CMU UCLA SDC USC NOAA GWC CASE
(a)
(d)
(b) (c)
(e)
Figure 1-27. Growth of the ARPANET. (a) December 1969. (b) July 1970. (c) March 1971. (d) April 1972. (e) September 1972.
In addition to helping the fledgling ARPANET grow, ARPA also funded re- search on the use of satellite networks and mobile packet radio networks. In one now famous demonstration, a truck driving around in California used the packet radio network to send messages to SRI, which were then forwarded over the ARPANET to the East Coast, where they were shipped to University College in London over the satellite network. This allowed a researcher in the truck to use a computer in London while driving around in California. This experiment also demonstrated that the existing ARPANET protocols were not suitable for running over different networks. This observation led to more research on protocols, culminating with the invention of the TCP/IP model and protocols (Cerf and Kahn, 1974). TCP/IP was specifically designed to handle communication over internetworks, something becoming increasingly important as more and more networks were hooked up to the ARPANET.
SEC. 1 EXAMPLE NETWORKS 59
To encourage adoption of these new protocols, ARPA awarded several con- tracts to implement TCP/IP on different computer platforms, including IBM, DEC, and HP systems, as well as for Berkeley UNIX. Researchers at the Univer- sity of California at Berkeley rewrote TCP/IP with a new programming interface called sockets for the upcoming 4 release of Berkeley UNIX. They also wrote many application, utility, and management programs to show how con- venient it was to use the network with sockets. The timing was perfect. Many universities had just acquired a second or third VAX computer and a LAN to connect them, but they had no networking software. When 4 came along, with TCP/IP, sockets, and many network utilities, the complete package was adopted immediately. Furthermore, with TCP/IP, it was easy for the LANs to connect to the ARPANET, and many did. During the 1980s, additional networks, especially LANs, were connected to the ARPANET. As the scale increased, finding hosts became increasingly expen- sive, so DNS (Domain Name System) was created to organize machines into do- mains and map host names onto IP addresses. Since then, DNS has become a generalized, distributed database system for storing a variety of information relat- ed to naming. We will study it in detail in Chap. 7.
NSFNET
By the late 1970s, NSF (the U. National Science Foundation) saw the enor- mous impact the ARPANET was having on university research, allowing scien- tists across the country to share data and collaborate on research projects. How- ever, to get on the ARPANET a university had to have a research contract with the DoD. Many did not have a contract. NSF’s initial response was to fund the Computer Science Network (CSNET) in 1981. It connected computer science de- partments and industrial research labs to the ARPANET via dial-up and leased lines. In the late 1980s, the NSF went further and decided to design a successor to the ARPANET that would be open to all university research groups. To have something concrete to start with, NSF decided to build a backbone network to connect its six supercomputer centers, in San Diego, Boulder, Cham- paign, Pittsburgh, Ithaca, and Princeton. Each supercomputer was given a little brother, consisting of an LSI-11 microcomputer called a fuzzball. The fuzzballs were connected with 56-kbps leased lines and formed the subnet, the same hard- ware technology the ARPANET used. The software technology was different however: the fuzzballs spoke TCP/IP right from the start, making it the first TCP/IP WAN. NSF also funded some (eventually about 20) regional networks that connected to the backbone to allow users at thousands of universities, research labs, libraries, and museums to access any of the supercomputers and to communicate with one another. The complete network, including backbone and the regional networks, was called NSFNET. It connected to the ARPANET through a link between an
SEC. 1 EXAMPLE NETWORKS 61
This arrangement meant that a packet originating on any regional network had a choice of backbone carriers to get from its NAP to the destination’s NAP. Con- sequently, the backbone carriers were forced to compete for the regional net- works’ business on the basis of service and price, which was the idea, of course. As a result, the concept of a single default backbone was replaced by a commer- cially driven competitive infrastructure. Many people like to criticize the Federal Government for not being innovative, but in the area of networking, it was DoD and NSF that created the infrastructure that formed the basis for the Internet and then handed it over to industry to operate. During the 1990s, many other countries and regions also built national re- search networks, often patterned on the ARPANET and NSFNET. These in- cluded EuropaNET and EBONE in Europe, which started out with 2-Mbps lines and then upgraded to 34-Mbps lines. Eventually, the network infrastructure in Europe was handed over to industry as well. The Internet has changed a great deal since those early days. It exploded in size with the emergence of the World Wide Web (WWW) in the early 1990s. Recent data from the Internet Systems Consortium puts the number of visible In- ternet hosts at over 600 million. This guess is only a low-ball estimate, but it far exceeds the few million hosts that were around when the first conference on the WWW was held at CERN in 1994. The way we use the Internet has also changed radically. Initially, applications such as email-for-academics, newsgroups, remote login, and file transfer dom- inated. Later it switched to email-for-everyman, then the Web and peer-to-peer content distribution, such as the now-shuttered Napster. Now real-time media dis- tribution, social networks (e., Facebook), and microblogging (e., Twitter) are taking off. These switches brought richer kinds of media to the Internet and hence much more traffic. In fact, the dominant traffic on the Internet seems to change with some regularity as, for example, new and better ways to work with music or movies can become very popular very quickly.
Architecture of the Internet
The architecture of the Internet has also changed a great deal as it has grown explosively. In this section, we will attempt to give a brief overview of what it looks like today. The picture is complicated by continuous upheavals in the businesses of telephone companies (telcos), cable companies and ISPs that often make it hard to tell who is doing what. One driver of these upheavals is telecom- munications convergence, in which one network is used for previously different uses. For example, in a ‘‘triple play’’ one company sells you telephony, TV, and Internet service over the same network connection on the assumption that this will save you money. Consequently, the description given here will be of necessity somewhat simpler than reality. And what is true today may not be true tomorrow.
62 INTRODUCTION CHAP. 1
The big picture is shown in Fig. 1-29. Let us examine this figure piece by piece, starting with a computer at home (at the edges of the figure). To join the Internet, the computer is connected to an Internet Service Provider, or simply ISP, from who the user purchases Internet access or connectivity. This lets the computer exchange packets with all of the other accessible hosts on the Internet. The user might send packets to surf the Web or for any of a thousand other uses, it does not matter. There are many kinds of Internet access, and they are usually distinguished by how much bandwidth they provide and how much they cost, but the most important attribute is connectivity.
Data center
Fiber (FTTH)
DSL
Dialup Cable
3G mobile phone
Tier 1 ISP
Other ISPs
Peering at IXP
POP Data path
Router
Cable modem CMTS
Backbone
DSLAM
DSL modem
Figure 1-29. Overview of the Internet architecture.
A common way to connect to an ISP is to use the phone line to your house, in which case your phone company is your ISP. DSL, short for Digital Subscriber Line, reuses the telephone line that connects to your house for digital data transmission. The computer is connected to a device called a DSL modem that converts between digital packets and analog signals that can pass unhindered over the telephone line. At the other end, a device called a DSLAM (Digital Sub- scriber Line Access Multiplexer) converts between signals and packets. Several other popular ways to connect to an ISP are shown in Fig. 1-29. DSL is a higher-bandwidth way to use the local telephone line than to send bits over a traditional telephone call instead of a voice conversation. That is called dial-up and done with a different kind of modem at both ends. The word modem is short for ‘‘modulator demodulator’’ and refers to any device that converts between digi- tal bits and analog signals. Another method is to send signals over the cable TV system. Like DSL, this is a way to reuse existing infrastructure, in this case otherwise unused cable TV
64 INTRODUCTION CHAP. 1
traffic so that each ISP can deliver some traffic to the other ISP without having to pay for transit. One of the many paradoxes of the Internet is that ISPs who pub- licly compete with one another for customers often privately cooperate to do peer- ing (Metz, 2001). The path a packet takes through the Internet depends on the peering choices of the ISPs. If the ISP delivering a packet peers with the destination ISP, it might deliver the packet directly to its peer. Otherwise, it might route the packet to the nearest place at which it connects to a paid transit provider so that provider can deliver the packet. Two example paths across ISPs are drawn in Fig. 1-29. Often, the path a packet takes will not be the shortest path through the Internet. At the top of the food chain are a small handful of companies, like AT&T and Sprint, that operate large international backbone networks with thousands of rout- ers connected by high-bandwidth fiber optic links. These ISPs do not pay for transit. They are usually called tier 1 ISPs and are said to form the backbone of the Internet, since everyone else must connect to them to be able to reach the en- tire Internet. Companies that provide lots of content, such as Google and Yahoo!, locate their computers in data centers that are well connected to the rest of the Internet. These data centers are designed for computers, not humans, and may be filled with rack upon rack of machines called a server farm. Colocation or hosting data centers let customers put equipment such as servers at ISP POPs so that short, fast connections can be made between the servers and the ISP backbones. The Internet hosting industry has become increasingly virtualized so that it is now common to rent a virtual machine that is run on a server farm instead of installing a physical computer. These data centers are so large (tens or hundreds of thousands of machines) that electricity is a major cost, so data centers are some- times built in areas where electricity is cheap. This ends our quick tour of the Internet. We will have a great deal to say about the individual components and their design, algorithms, and protocols in subsequent chapters. One further point worth mentioning here is that what it means to be on the Internet is changing. It used to be that a machine was on the Internet if it: (1) ran the TCP/IP protocol stack; (2) had an IP address; and (3) could send IP packets to all the other machines on the Internet. However, ISPs often reuse IP addresses depending on which computers are in use at the moment, and home networks often share one IP address between multiple computers. This practice undermines the second condition. Security measures such as firewalls can also partly block computers from receiving packets, undermining the third condition. Despite these difficulties, it makes sense to regard such machines as being on the Internet while they are connected to their ISPs. Also worth mentioning in passing is that some companies have interconnected all their existing internal networks, often using the same technology as the Inter- net. These intranets are typically accessible only on company premises or from company notebooks but otherwise work the same way as the Internet.
SEC. 1 EXAMPLE NETWORKS 65
1.5 Third-Generation Mobile Phone Networks
People love to talk on the phone even more than they like to surf the Internet, and this has made the mobile phone network the most successful network in the world. It has more than four billion subscribers worldwide. To put this number in perspective, it is roughly 60% of the world’s population and more than the number of Internet hosts and fixed telephone lines combined (ITU, 2009). The architecture of the mobile phone network has changed greatly over the past 40 years along with its tremendous growth. First-generation mobile phone systems transmitted voice calls as continuously varying (analog) signals rather than sequences of (digital) bits. AMPS (Advanced Mobile Phone System), which was deployed in the United States in 1982, was a widely used first- generation system. Second-generation mobile phone systems switched to trans- mitting voice calls in digital form to increase capacity, improve security, and offer text messaging. GSM (Global System for Mobile communications), which was deployed starting in 1991 and has become the most widely used mobile phone system in the world, is a 2G system. The third generation, or 3G, systems were initially deployed in 2001 and offer both digital voice and broadband digital data services. They also come with a lot of jargon and many different standards to choose from. 3G is loosely defined by the ITU (an international standards body we will discuss in the next section) as providing rates of at least 2 Mbps for stationary or walking users and 384 kbps in a moving vehicle. UMTS (Universal Mobile Telecommunications System), also called WCDMA (Wideband Code Division Multiple Access), is the main 3G system that is being rapidly deployed worldwide. It can provide up to 14 Mbps on the downlink and almost 6 Mbps on the uplink. Future releases will use multiple antennas and radios to provide even greater speeds for users. The scarce resource in 3G systems, as in 2G and 1G systems before them, is radio spectrum. Governments license the right to use parts of the spectrum to the mobile phone network operators, often using a spectrum auction in which network operators submit bids. Having a piece of licensed spectrum makes it easier to de- sign and operate systems, since no one else is allowed transmit on that spectrum, but it often costs a serious amount of money. In the UK in 2000, for example, five 3G licenses were auctioned for a total of about $40 billion. It is the scarcity of spectrum that led to the cellular network design shown in Fig. 1-30 that is now used for mobile phone networks. To manage the radio interference between users, the coverage area is divided into cells. Within a cell, users are assigned channels that do not interfere with each other and do not cause too much interference for adjacent cells. This allows for good reuse of the spec- trum, or frequency reuse, in the neighboring cells, which increases the capacity of the network. In 1G systems, which carried each voice call on a specific fre- quency band, the frequencies were carefully chosen so that they did not conflict with neighboring cells. In this way, a given frequency might only be reused once
Andrew S. Tanenbaum - Computer Networks-10
Course: Python Programming Lab (SOC-2)
University: Adithya Institute of Technology

- Discover more from: